Online B2B Marketplace of Suppliers & Service Providers. Discover Verified Products
iCognative
Price: On Request
Min. Order: On Request
Min. Order: On Request
Product Description
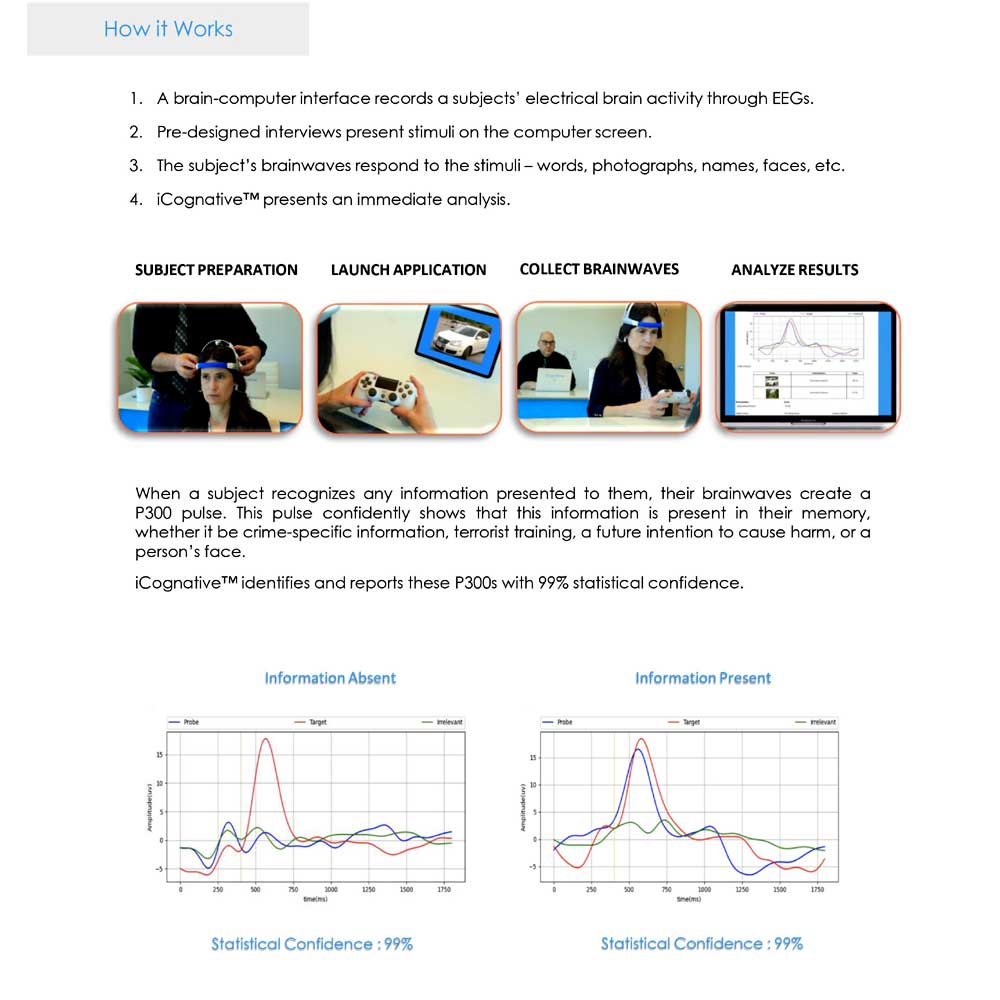
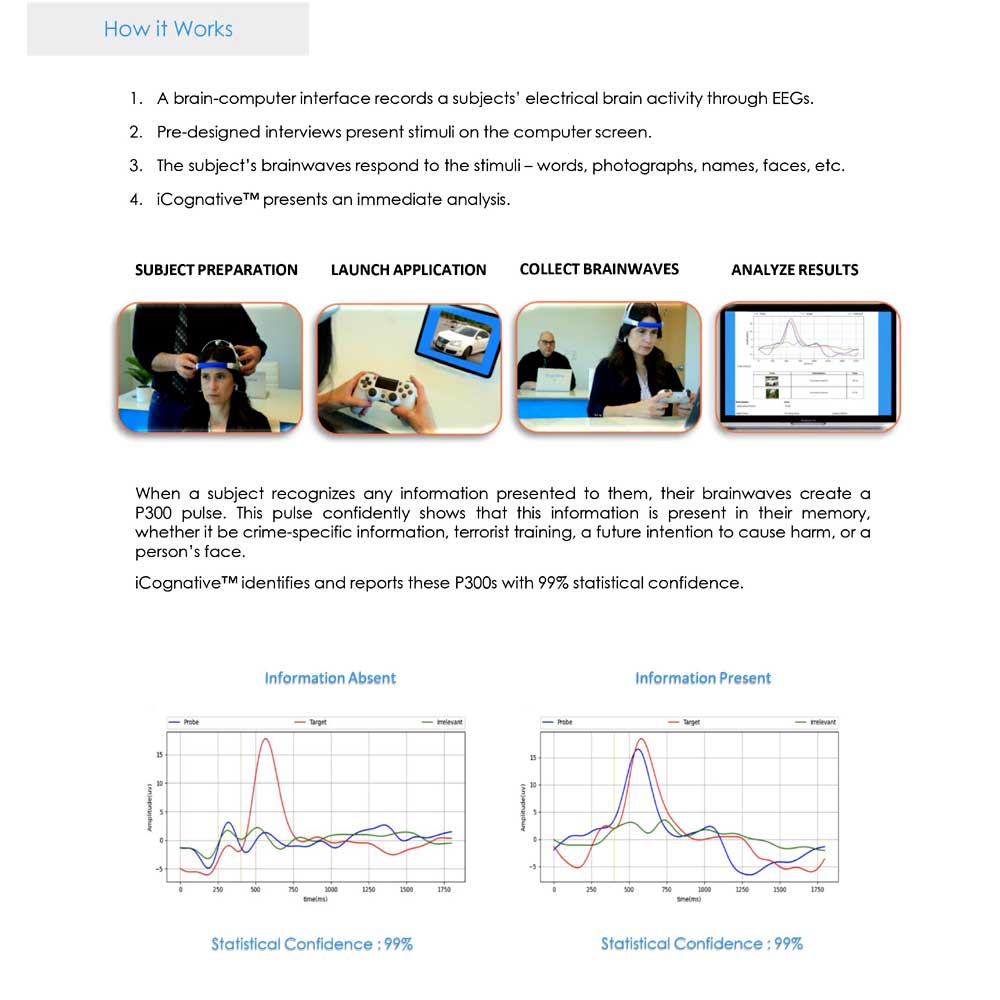
PRECISION, ACCURACY, RELIABILITY
Relies on brain information processing that detects distinct change in electrical activity when a human brain responds to the sight of familiar stimuli
Results always have high accuracy rates with over 99% statistical confidence
Zero false positives and negatives
Purpose-built to eliminate countermeasures
ADVANCED SCIENTIFIC TECHNIQUE
Proprietary algorithms embedded in software to collect unique electrical signal from the brain
P300 response is an involuntary neurological response, not subject to any manipulative behavior
P300 electrical activity starts anywhere from 300 milliseconds to 800 milliseconds after a recognized stimulus
A breakthrough capability to detect concealed information
INTELLIGENCE COLLECTION DISCIPLINE
Matches information from the crime scene with information stored in the subject’s brain repository
Fast data-processing ensures immediate delivery of results
Lightweight and minimal equipment designed to guarantee easy portability and setup
Ease of implementation from stimulus creation to setup to testing methodology
USER-FRIENDLY SYSTEM & INTERFACE
Simple yet powerful system features define the ease of operation
Intuitive and beautiful interface created with thoughtfulness and intention
Advanced software architecture supported by the latest, durable, and high-quality technologies
Accommodates customization and unique needs of users
Ease of operation defined by simple and powerful system features
WIDE-RANGE APPLICATIONS
Accurately distinguishes who participated in, planned, or perpetrated criminal acts, directly or indirectly
Supports investigators and intelligence units to identify which criminal networks suspects belong to, including terrorists in sleeper cells
Helps pinpoint the chain of command of a suspect for any criminal network
Protects classified information by detecting which criminals harbor unauthorized knowledge
Validates missing link between available information and evidence from various sources and knowledge concealed in the brain
Screens illegal intruders and threat actors with reliable group-based knowledge to effectively assess risk